With a well-structured Information Security Management System (ISMS), your organisation will have its security properly in place.
ISMS software
Every day, your organisation works with sensitive information and personal data, both from customers and from within your own organisation. Naturally, you want to prevent this information from falling into the wrong hands. That's why effective information security is essential. It protects your data against harmful attacks.
However, information security can quickly become complex. Implementing security standards such as ISO 27001, NEN 7510, ISO 27701 or the GDPR require specialised knowledge in the areas of IT, business and legal matters. Because these security standards affect almost all aspects of business operations, it is difficult to organise this and keep an overview.
Good ISMS software helps you meet the various security standards and provides the support you need to work in compliantly, efficiently and demonstrably securely.
Stay in control with the ISMS tool Base27
Characteristiscs of the right ISMS tool
ISMS software is a digital tool that helps organisations establish, maintain and improve an Information Security Management System (ISMS). It enables a structured and centralised approach to information security, risk analysis, compliance and continual improvement, fully aligned with international standards such as ISO 27001, NEN 7510 and the BIO.
While ISMS consists of the policies, processess, procedures and technologies that safeguard information security within your organisation, an ISMS tool provides the digital support for this system. It centralises information, facilitates automation and significantly accelerates audit and compliance processes.
What is the difference between an ISMS and ISMS software?
An ISMS compromises the processes themselves, while an ISMS system provides the support. In short, an ISMS is the "what", and ISMS software is the "how".
- ISMS (Information Security Management System): the formal framework through which an organisation structures its information security, including policy documents, risk analysis, controls and improvement cycles.
- ISMS software: the digital tool that facilitates and manages the elements of an ISMS. This includes dashboards, workflows, notifications, templates, logging and reporting.
Which standards and laws does ISMS software cover?
A good ISMS tool not only helps you comply with ISO 27001, but also supports other relevant laws and related information-security frameworks, such as:
- ISO/IEC 27000 series, including ISO/IEC 27001:2022
- GDPR - the European privacy regulation
- NIS2 - the Network and Information Security Directive
- SOC 2 - the compliance framework for securely managing customer data
- PCI DSS - for organisations processing payment data
- DORA - for financial institutions and ICT providers within the EU
With built-in templates, frameworks and control sets, ISMS software helps you demonstrate compliance with these standards, including automatically generated audit reports.
How does ISMS software relate to ISO 27001?
ISO 27001 is the international standard for information security management. Holding the certificate demonstrates that your organisation's information security is in order. An ISMS tool such as Base27 supports you in establishing information security in line with ISO 27001 through:
- Mapping risks and performing risk assessments
- Drafting and managing information security policies
- Implementing controls
- Conducting internal audits
- Documenting management reviews
- Supporting the PDCA cycle (Plan-Do-Check-Act)
An ISMS tool is not a requirement for ISO 27001, but in practice makes the process much more manageable, efficient and easier to follow.
What are the key features of ISMS software?
Powerful ISMS software, such as Base27, offers a wide range of features that elevate your information security to the next level. We've listed the most important functionalities for you below.
Policy framework
Risk management
Control of information systems
Register of processing of personal data
Supplier Management
Support internal and external audits
Expandable with organisation-specific features
Continuous improvement using PDCA
Incident Management
Register of operating assets
Support for different standards frameworks
Integration with other systems
Benefits of an ISMS tool such as Base27
Using ISMS software such as Base27 offers significant benefits, both strategically and operationally:
- Faster implementation: Automation and clear overviews help you meet compliance requirements more quickly and avoid costly fines.
- Efficiency and centralised control: Fewer scattered spreadsheets and emails, you have one central place for all your ISMS activities.
- Trust from customers and stakeholders: Transparency and demonstrable controls increase confidence in your organisation.
- Ease of use: Base27 is user-friendly and offers an intuitive interface.
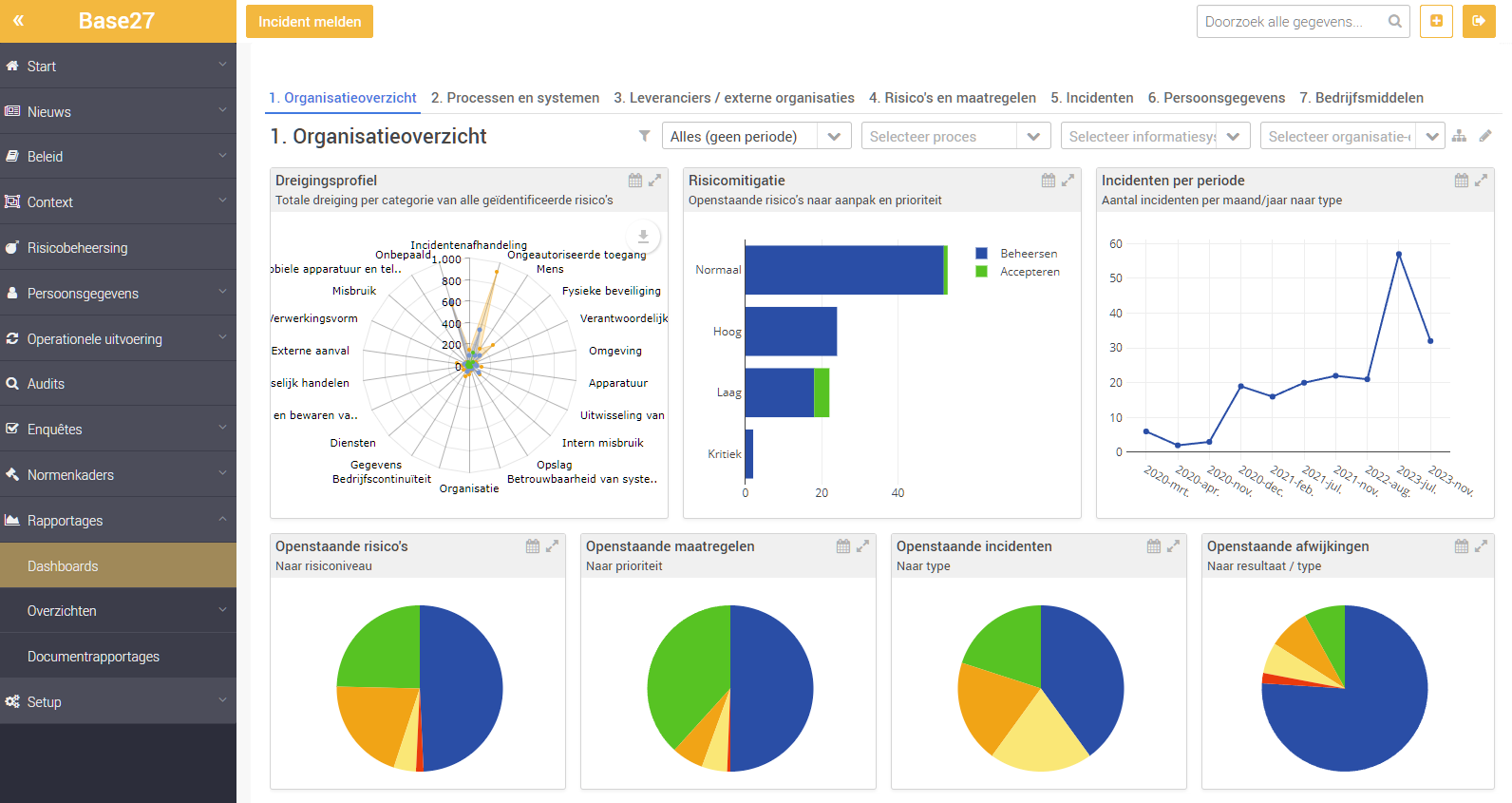
Dashboards &
Reports
- Comprehensive reports giving you insight into the status of your information security at all times;
- Dashboards for quick and easy insight into the status of your information security;
- Insight by department, or across the board;
- Filters and sorting;
- Exports to Microsoft Excel or Word;
- Analysis in pivot tables.
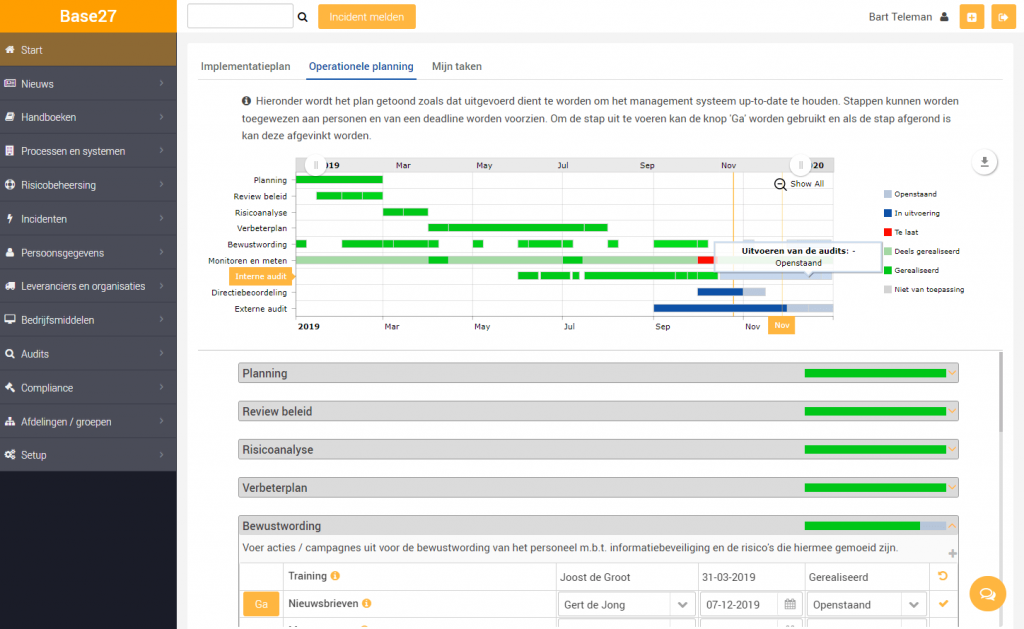
Planning
- See at a glance which information security maintenance tasks need to be performed throughout the year and what the status is;
- Easily assign tasks and monitor progress;
- The plan can be flexibly expanded and repeated annually.
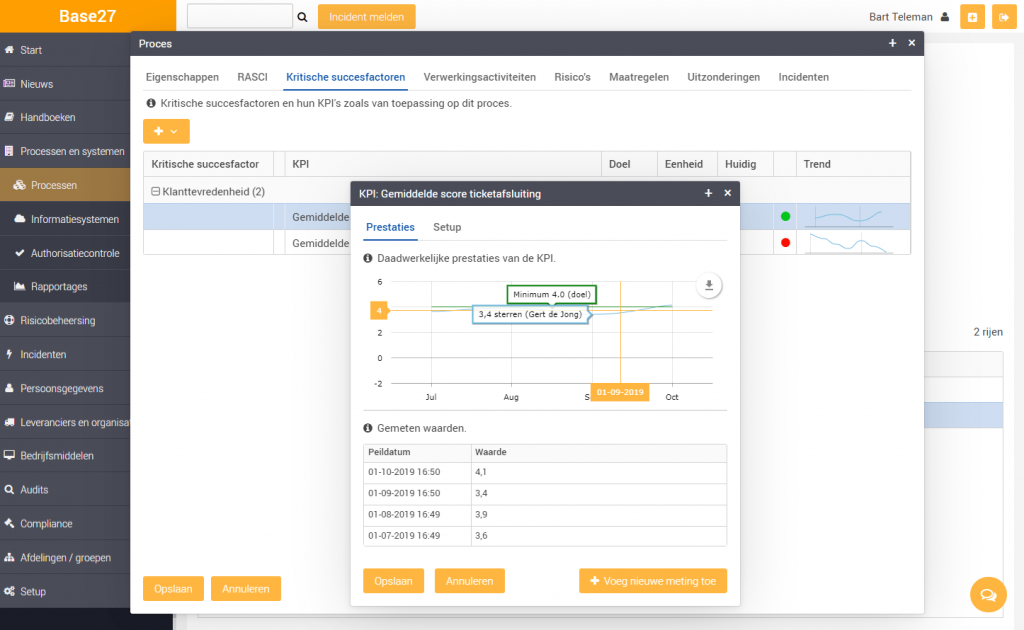
Processes & KPIs
- Establish overview of processes and related information systems;
- Set and manage critical success factors and KPIs (Key Performance Indicators);
- Compliance with standards is automatically made transparent.
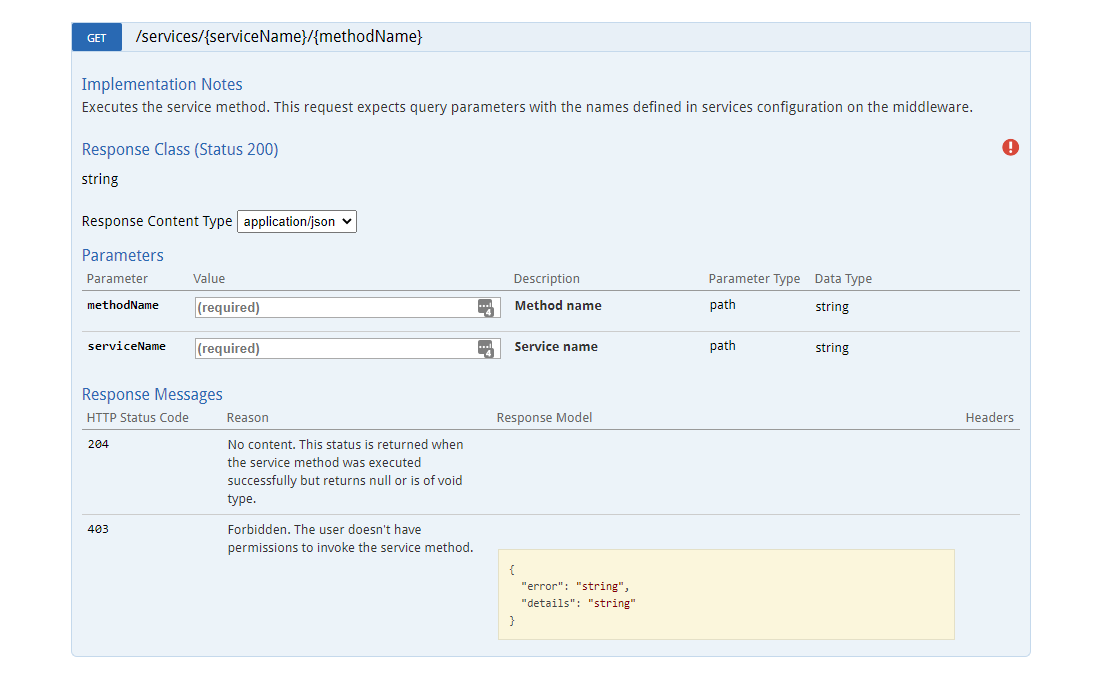
Single Sign-on
- Base27 is excellent for integrating within your organisation, for example by using SAML, to allow your employees to access the application without logging in again;
- REST interface to link data from other sources. Through this capability, incidents from for example your ITSM can be read in or updates sent.
How do I choose the right ISMS tool?
To establish and maintain strong information security, you need a sustainable solution that provides clarity and insight in an accessible way. Choosing the right ISMS tool for your organisation depends on factors such as organisation size, compliance requirements and objectives, the IT environment and your budget. It is wise to consider the following questions when making your choice:
- Does the ISMS tool support relevant standards such as ISO 27001 and NIS2?
- Is the software user-friendly and customisable?
- What integration options does the system offer?
- Is the ISMS tool scalable and able to grow with your organisation?
- What is the pricing model of the ISMS solution?
In addition, an ISMS system should be affordable and based on best practices. Above all, it must align with the various standards your organisation aims to be certified for.
How does the implementation of an ISMS work?
Implementing an ISMS is closely linked to achieving ISO 27001 certification. A key part of the certification process is the implementation and maintenance of an effective ISMS. ISMS software such as Base27 supports this and can be used to guide the implementation smoothly.
For the implementation of an ISMS and the certification of ISO 27001, the following steps are typically carried out:
- Establishing the information security policy: This policy defines the rules regarding data protection, measures to safeguard security, the steps to take in the event of incidents, and the roles and responsibilities involved.
- Analysing information systems and processes: It is essential to classify all business information and inventory all information systems within the organisation.
- Conducting a risk analysis: Identify all potential risks and threats through a risk assessment.
- Implementing risk mitigation measures: Determine how to control the risks identified in the risk assessment and how to act if a risk materialises.
- Assessing the residual risk: Once all threats and risks have been identified, the residual risk can be determined — the risk that remains after all measures have been taken.
- Addressing GDPR requirements: Storing, exchanging and managing personal data requires compliance with the GDPR. This step ensures that these legal obligations are met.
- Increasing employee awareness: To maintain strong information security, employees need to be aware of the policies and their role. Provide training and communicate clearly.
- Implementing internal control: Internal control helps ensure the effectiveness of information security, identify new risks and continuously improve security.
- Preparing for ISO 27001 certification: Once all steps have been completed and the ISMS is properly implemented, preparations for certification can begin.
- Organising the external audit and certification: When everything is in place, you can select an auditor to carry out the certification audit.
Base27: the ISMS solution
Good ISMS software supports your information security efforts and helps you establish guidelines and drive continual improvement. When you choose Base27 as your ISMS, you benefit from a policy framework, compliance standards and the associated improvement processes.
In addition, Base27 provides operational support to help you bring information security within your organisation up to standard. Base27 monitors and records all processes related to information security.
Your ISMS always up to date with Base27
Setting up an ISMS in line with ISO 27001 and other relevant standards for your organisation can quickly become complex and time-consuming. Base27 offers the solution: a powerful ISMS platform that enables you to establish information security in accordance with ISO 27001 or NEN 7510 in no time. This includes support for privacy protection in line with the GDPR and ISO 27701.
From risk analysis to reporting, Base27 provides one central system that allows you to easily perform risk assessments, internal audits and other evaluations. It also supports additional frameworks such as ISO 9001 and ISO 14001, and even offers support for ISAE 3402 reporting.
Thanks to Base27, rushed updates and manual work are a thing of the past. The standards are instantly applicable within your organisation, ensuring your ISMS is always up to date.

 English
English
 Nederlands
Nederlands