Base27 features
Base27 is a clear online software solution that makes it easy and convenient to access all information related to your organisation's information security and privacy protection.
Suitable for security officers, privacy officers, information managers, internal auditors etc. as well as all your employees.
Base27 is fully aligned with ISO 27001 and NEN 7510 and offers support for various standards frameworks.
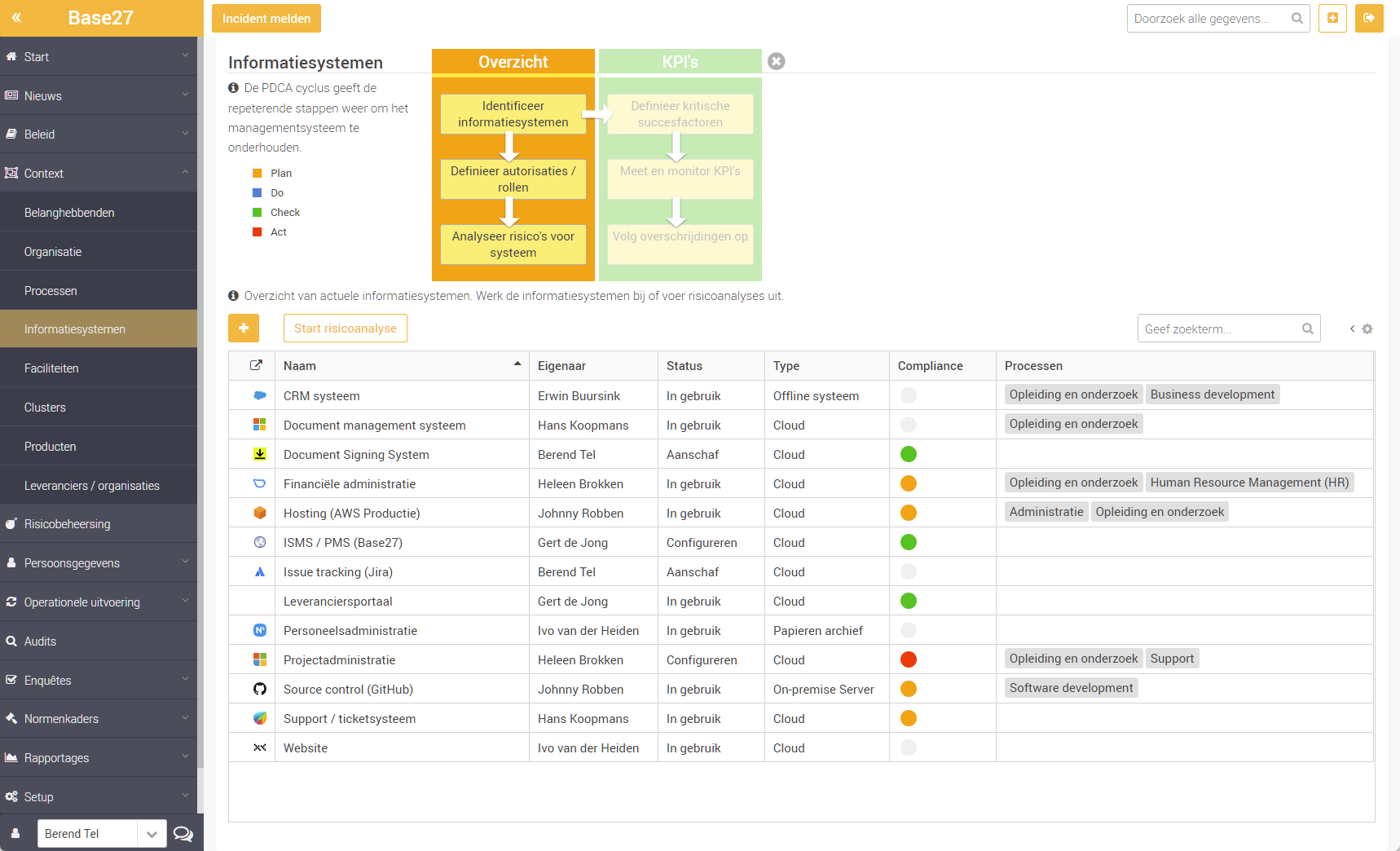
Information Systems
Understanding the processes and information systems used is the first step for adequate information security. With a clear overview of all information sources, you keep a grip on things. And with control and reporting capabilities, including a BIV and authorisation matrix, you stay secure.
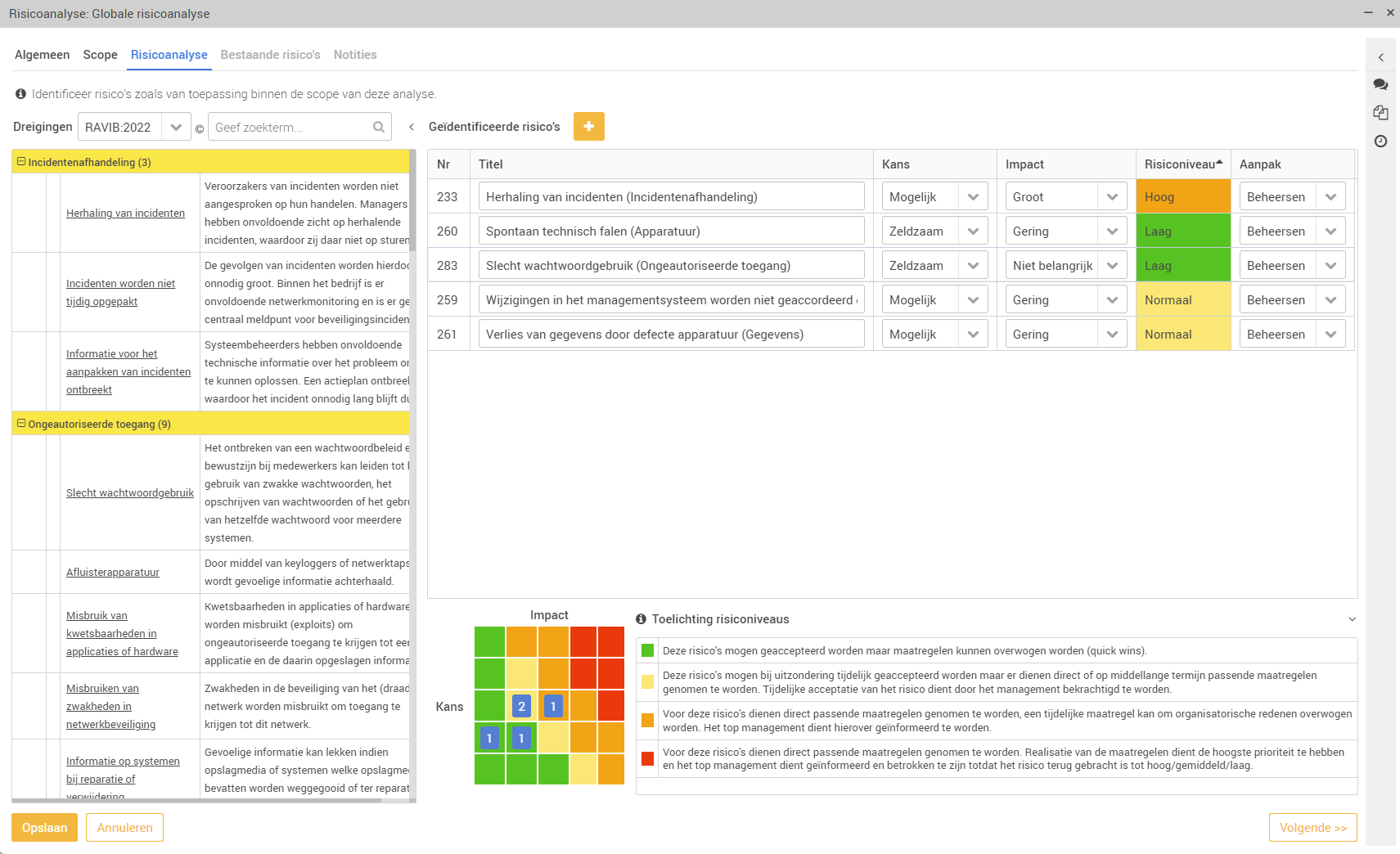
Risk Management
Comprehensive risk analyses based on processes, information systems and/or suppliers. With threat models such as MAPGOOD or the OWASP Top 10, you quickly identify risks and draw up measures to mitigate the risk. Progress monitoring and risk evaluation then ensure that these are adequately addressed.
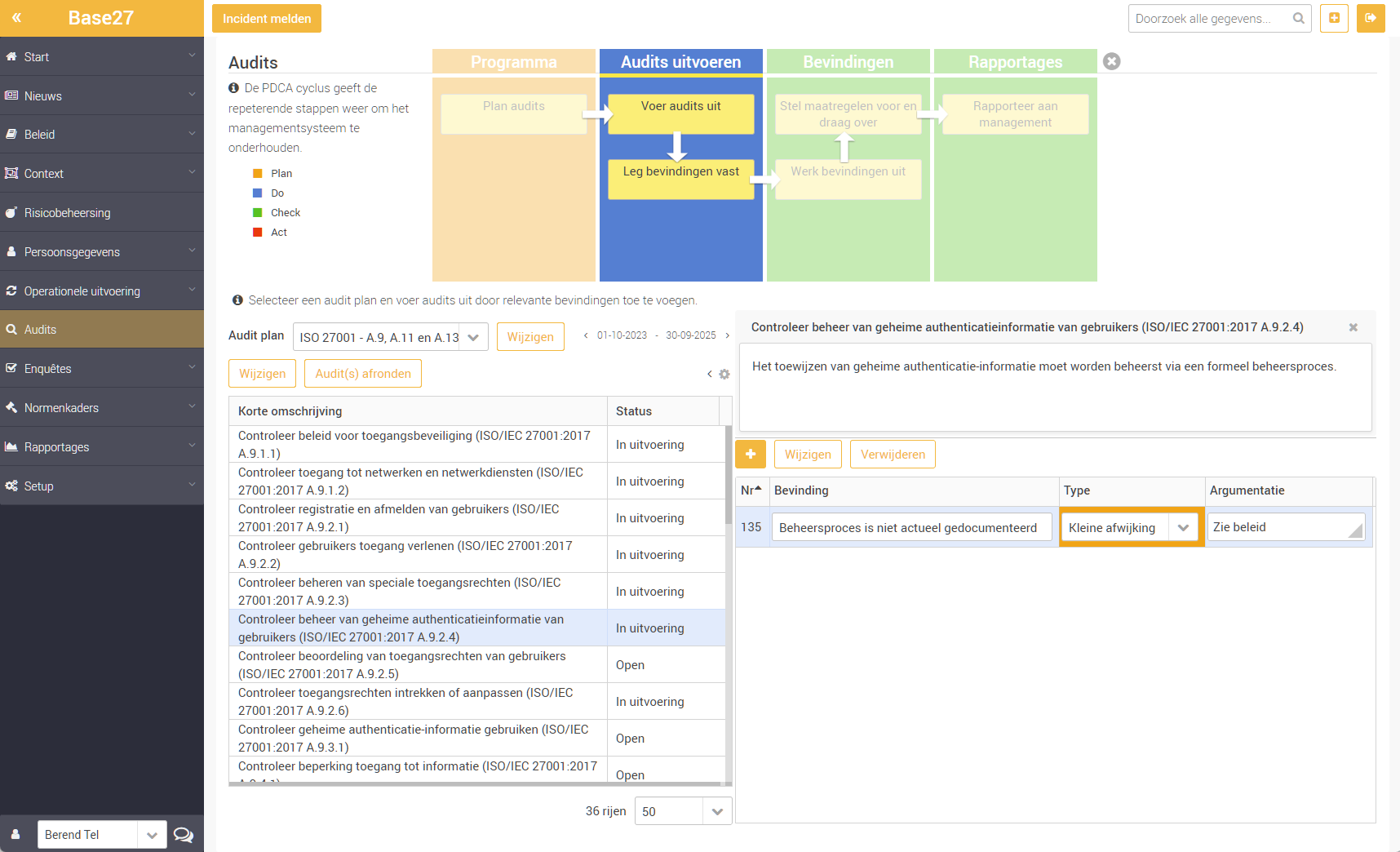
Internal and External Audits
By periodically performing internal / external audits on standards frameworks and your own policy, compliance remains guaranteed. You supplement findings and non-conformities with new countermeasures. Everything can be summarised in automated audit reports.
And many other features
- Management of policies in the form of manuals;
- Framework with full ISO27001 coverage;
- Information clearly displayed.

Processes and KPIs
- Establish processes and related information systems;
- Establish and manage objectives and KPIs (Key Performance Indicators);
- Compliance with the standard is automatically made transparent.
.png?width=55&height=67&name=Verwerkingsregister%20(AVG).png)
Processing Register (GDPR)
- Establish processing register in accordance with the GDPR;
- Conducting Data Protection Impact Assessments (or DPIAs);
- Establishing processor agreements;
- Record data breaches and collect all information required for reporting to the privacy authorities;
- Capabilities for the registration and handling of data subject requests.

Implementation and Certification
- Implementation plan for an ISO 27001 certification, for example. This plan easily helps you through the necessary steps to certification, including:
- Defining policy objectives;
- Inventory of systems and assets;
- Risk analysis and management;
- Internal control (audits);
- Preparation of a Statement of Applicability (SoA).
- Migration plan to transfer an existing information management system to Base27, or an GDPR specific implementation focusing on privacy protection.

Operational Planning
- See at a glance which information security maintenance tasks need to be performed throughout the year and what the status is;
- Easily assign tasks and monitor progress;
- The plan is flexibly expandable and can be repeated annually;
- It is also possible with the same functionality to draw up an execution plan for, for example, implementation or migration of (parts of) the information security.

Management Reports
- Reporting to management on all matters related to information security or privacy protection is easily accomplished using the document reports within Base27. The report is automatically compiled based on selected data;
- All data is available for reporting: information systems, suppliers, risks, measures, incidents, processing et cetera;
- Easily print or export to Microsoft Word. Output can be based on templates with your corporate identity.
Wondering how these features can help your organisation?

Enterprise Features
- Insight and direction by department or business unit;
- Organising compliance within a broad user organisation using questionnaires.
- Informing employees about developments in the field of information security and privacy protection within your organisation by means of internal newsletters.
- Of course, insight into the extent to which the newsletters are actually read is not lacking.

Standards and Accountability
- Support for various standards:
- Information security, including: ISO 27001, ISO 27002, NEN 7510, BIO, ISO 27017/18, COBIT5
- Privacy protection, including: ISO 27701, AVG (GDPR)
- Quality assurance, including: ISO 9001, HKZ
- Other, including: ISO 14001
- Link to policies, processes, information systems, as measures for risks et cetera;
- Statement of Applicability (SoA);
- Internal audits easily based on the declaration of applicability;
- Direct insight into the progress of the implementation through reports.
Supplier Management
- Clearly name and test criteria on which you select suppliers;
- Periodic assessment of suppliers based on selected criteria;
- In addition to suppliers, registration and management of, for example, customers and other organisations.
Asset Management
- Record hardware, software, licenses, access assets and contracts, among others;
- If applicable, issue and intake records can be kept as well as renewal / depreciation records;
- Own types of assets can be dynamically added.

Calamity Plans
- Prepare for calamities by defining how such calamities should be handled and who is responsible;
- Regular monitoring of implementation/operation of business continuity plans.

Dashboards and Reports
- Dashboards for quick and easy insight into the status regarding information security;
- Insight across the whole or by segment (department, system, etc.);
- Filters and sorting;
- Exports to Microsoft Excel or Word;
- Analysis in pivot tables.
- Overviews and analysis of all information in Base27;
- Comprehensive reports allowing you to understand the status of the management system at all times.

Single Sign-On and Integration
- Base27 is excellent for integrating within your organization, for example by using Single Sign-On (based on SAML) to allow your employees to access the application without logging in again;
- REST API to link data from other sources. Through this capability, for example, incidents from your ITSM can be synchronised or comments sent.

Online support
- Direct contact with our support staff;
- Answers to questions regarding the use of Base27 but also for substantive questions regarding information security and privacy protection.

Security
- The application is continuously monitored and security updates are applied daily as needed;
- Default login is based on strong passwords and two-factor authentication;
- Regular backups of data and testing its integrity;
- Data is stored encrypted at our partner in the Netherlands.




Professional, well structured and practical solution
The first supplier ever that is always available and understands our objectives
Base27 makes compliance clear and simple to enforce
Easy accessible system for managing our ISMS
ISMS for your organisation
Base27 monitors and records your processes. It is both an information security management system (ISMS) and privacy management system (PMS), which gives you a handle on the many and often complex aspects of information security and privacy protection. Base27 supports policy-making, communication, risk analysis and control as well as registration of assets, among other things.

 English
English
 Nederlands
Nederlands